Cyberoam Hacking Software
On Demand Webinars. Understanding Cryptography Simple and old-fashioned cyber crime is now a thing of past. Today's CIOs and enterprise security executives always remain wary of what lurks in their organizational networks.
Measuring Security ROI The term ROI continues to heat the debates across boardrooms vis-a-vis spends on IT and network security. As most investments allocated towards security focus on risk avoidance, it has become a challenge for CIOs and CSOs to quantify security ROI. Optimizing Security for Azure Cloud services The advent of cloud computing is forcing companies to re-evaluate their IT strategy. Not being assured with the benefits that cloud offers, many enterprises are leery of migrating critical enterprise applications to the cloud due to security concerns and business continuity.
Hello Friends, today i am going to explain you How to hack crack or bypass cyberoam websense and all other security firewalls that college, institutions, offices use to block websites at their respective places. Most of colleges, school and offices nowadays prefers a hardware firewall to block the users to access the restricted websites. Most of my friends have asked me about that how to access blocked websites or bypass cyberoam or simply cracking the cyberoam to access restricted websites in their college and offices, i have explained some methods earlier also but those loopholes are now fixed and those methods to hack cyberoam and websense doesn't work effectively now and also hacking through proxy is quite tedious task as first of all we have to search for good working proxy websites which in itself is a very tedious task, and most of times it is also blocked. So it actually wastes lot of our precious times and most important daily. So why don't we have a permanent solution for it.

The method that i will explain today is really awesome and doesn't require much effort and thus its quite easy and the most important its 100% working. So friends read on for detailed hack.
Hacking or bypassing or cracking cyberoam For hacking Cyberoam or Websense you must know How cyberoam and websense works? If you know how it works then you can easily find flaws in it and hack or bypass it very easily. So friends lets learn how cyberoam actually works.
Cyberoam is a 8 layer hardware firewall that offers stateful and deep packet inspection for network and web applications and user based identity security. Thus the firewall is quite secured. Now how we can hack that 8 layer security its the main important question here, as i have mentioned above that main working and blocking of any website or application by cyberoam is basically done at deep packet inspection step, now here the flaw in any security firewall lies, also in case of cyberoam and websense too. Epa corrosion control guidance.
They block all websites by parsing their content and if their content contains the restricted keywords then they block that websites. They also use category blocking which also works on same concept. The flaw is with websites that uses SSL feature, the websites that contains SSL lock i.e. The websites that uses https are not blocked by them.
They have to block these websites manually which is a very hectic task and believe me nobody blocks them. So the proxy websites that uses https i.e. SSL proxies are also not blocked by these websites.
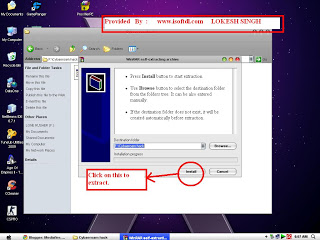
Only those proxies are blocked which are known or being heavily used. But the tool that i give you create SSL proxies by itself that means its proxies cannot be blocked. So friends this tool rocks. Things that we need to hack cyberoam, websense and any such such hardware firewall: 1. TOR browser ( a anonymous web browser like Mozilla which has inbuilt proxy finder that bypasses the websites easily that are being blocked by cyberoam or websense). A USB or pendrive ( where you will keep the portable version of TOR browser) 3. If USB drives are disabled we will use different drive for its installation.
(also portable version of TOR can be executed from any place). Steps to hack Cyberoam: 1. Download the TOR web browser. Now install the TOR web browser. In case of portable version it will extract. Now open the TOR browser and start surfing your favorite website like facebook, orkut, gmail.everything at you office.
Cyberoam Vpn
That's all the hack. I hope you all have liked it. Note: Have a portable version in your pen drive or USB drive and enjoy where ever you want. Click to expand.Is it possible to boot the machine from a USB drive?
You may have to enter the BIOS menu (press DELETE, F2 or some other key before the operating system takes over) to enable it. If you can do that, there are several Linux distros specifically crafted to fit on a CD or USB drive: Also, about doing that. There are a lot of disadvantages to rebooting. It's a hassle, you may not be able to access your school network resources, and you may stand out as a renegade (maybe good or bad ) if your screen is visible. But it will kill two birds with one stone by freeing you from Windows and allowing you to use whatever software you want.
Is it possible to boot the machine from a USB drive? You may have to enter the BIOS menu (press DELETE, F2 or some other key before the operating system takes over) to enable it. If you can do that, there are several Linux distros specifically crafted to fit on a CD or USB drive: Also, about doing that. There are a lot of disadvantages to rebooting. It's a hassle, you may not be able to access your school network resources, and you may stand out as a renegade (maybe good or bad ) if your screen is visible.
But it will kill two birds with one stone by freeing you from Windows and allowing you to use whatever software you want. I know that is not much my business but i will ask: why you all try to surf to restricted web pages using you corporate network? I don't really give a damn. I think that you all just will make the IT staff to run little bit and in the end they will find the cheater. In the end of everything think about that, if someone will find the way to get into your corporate network, still some personal information and get advantage of it, in this case they will check every single computer in the office/classroom or whatever and some one will be in trouble after. The best solution, safest, easiest is to get your self your own laptop, phone and use 3g hotspot.
In my case i have a Alfa network wireless adapter with capability to inject packets, i brute forced the neighbor wifi AP and now i use it when i need, changed my mac address, just in case and now i am free from any judgment. Please remember your business need to be secured.
Cyberoam Configuration
1.Facebook is a target for many hackers 2.porn sites are like Whores in Bangkok - so much pleasure and a lot of hidden surprises. 3.torrents are good for free software but most of them are infected with some crap. 4.the internet is a wild west, so dont help intruders to get in to your castle. Keep it clean.